When I first explored integrating Amazon Elastic Kubernetes Service (EKS) with AWS services like S3, the complexity of permissions was quite daunting. That is when I discovered Amazon EKS Pod Identity, a tool that greatly simplified this task. In this article, I will share my experience using EKS Pod Identity to grant an EKS application the necessary permissions to work with an S3 bucket.
Prerequisites
To get started, here is what I made sure I had in place:
- An active AWS account with access to EKS and S3.
- A running Amazon EKS cluster, version 1.24 or higher.
- AWS CLI installed and configured.
- kubectl set up for my EKS cluster.
- Docker installed for application containerization.
- A Python environment for script testing.
- An existing Amazon S3 bucket.
- Basic knowledge of Kubernetes.
Now, let us dive into my steps to set up this integration.
Define IAM Role Permissions
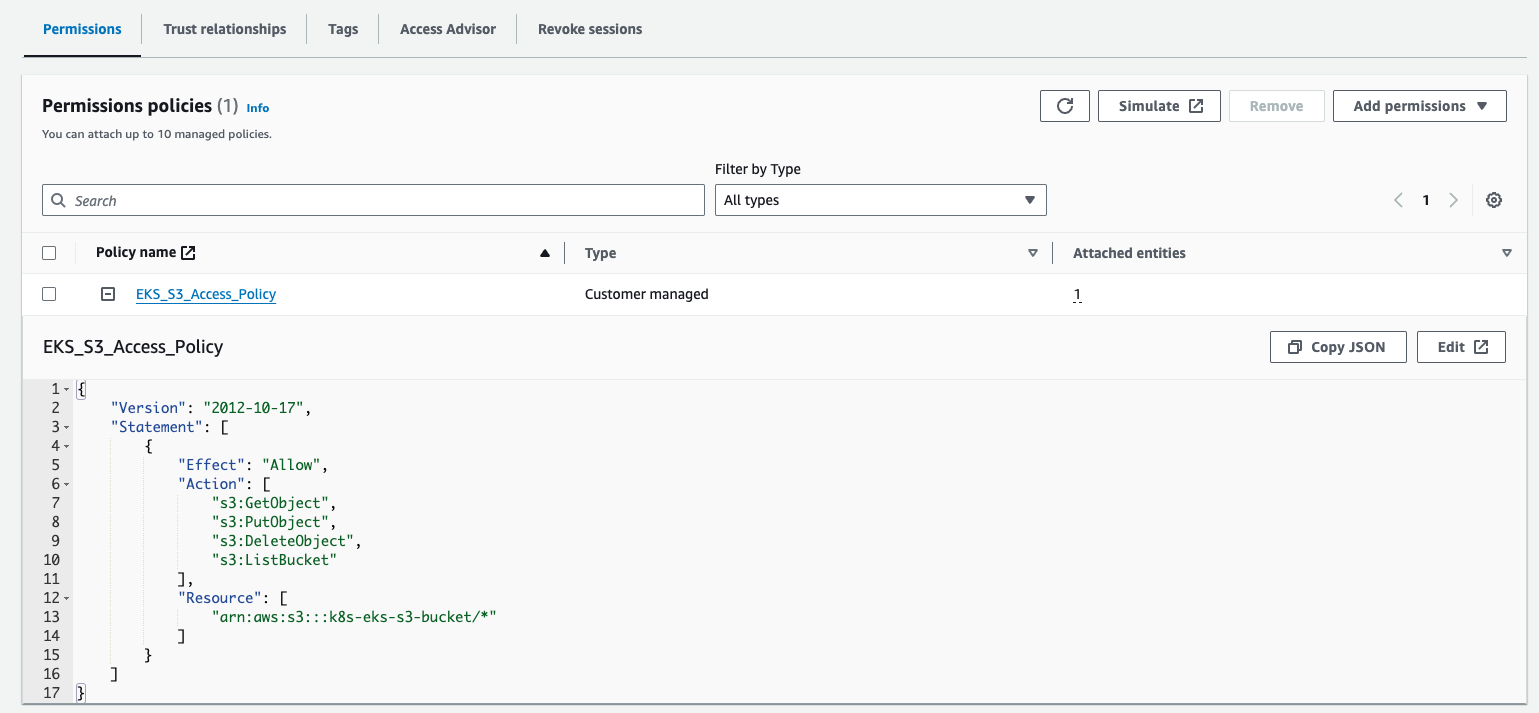
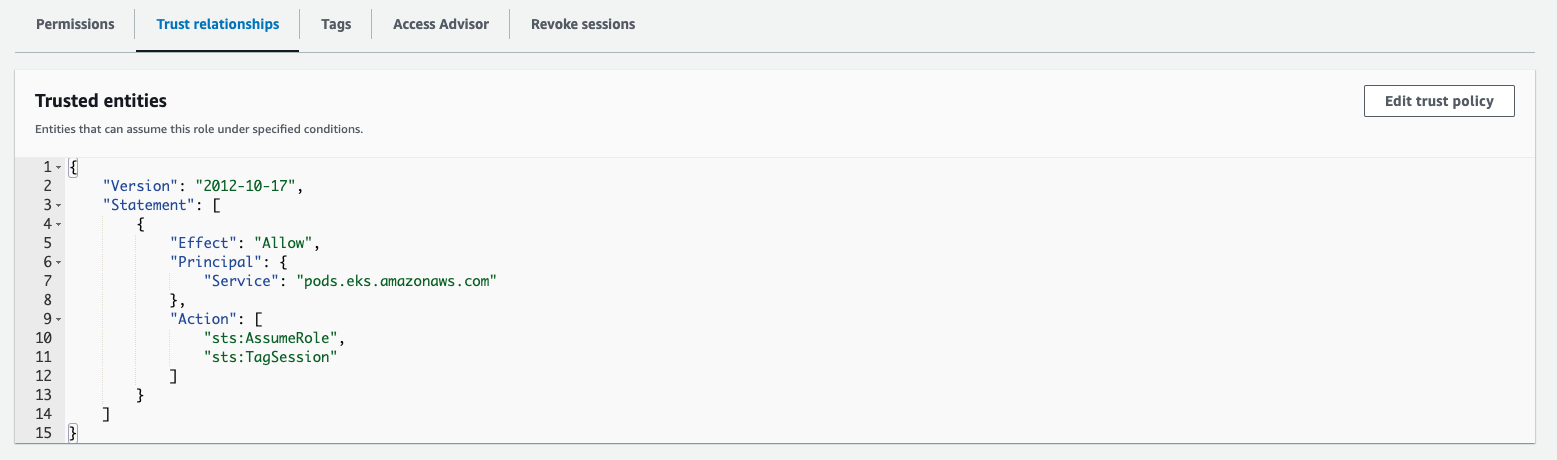
First, I needed to create an IAM role granting permission to access my S3 bucket. IAM role was crucial for running my applications smoothly. I set up the role and configured its trust policy to allow pods.eks.amazonaws.com as the principal, using a specific IAM template tailored for this setup.
Install EKS Pod Identity Agent
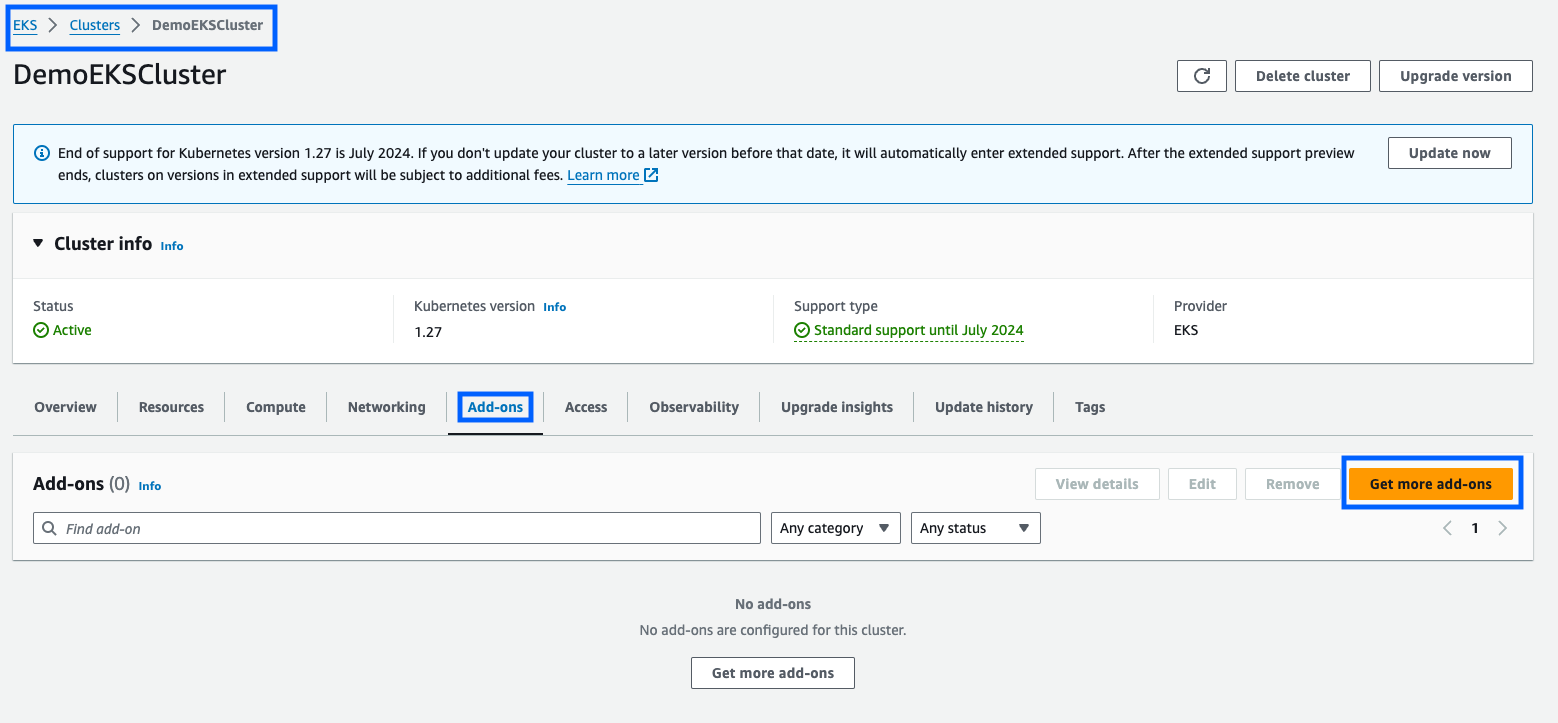
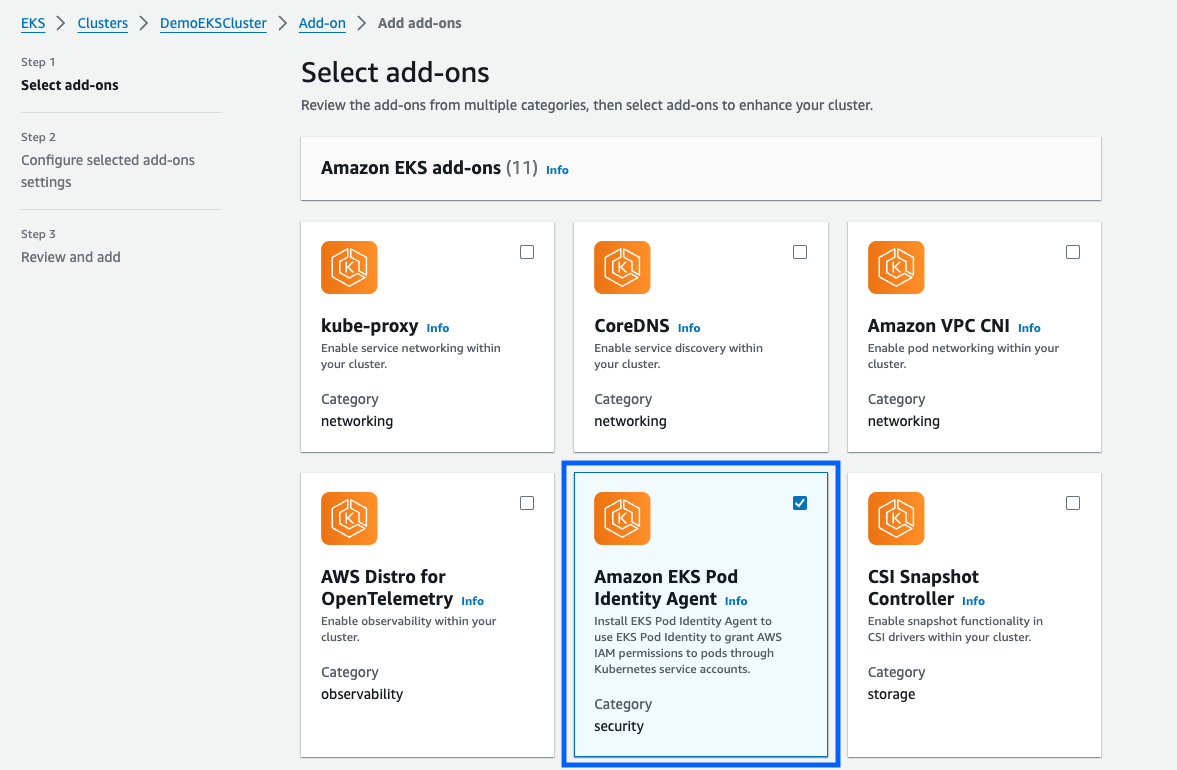
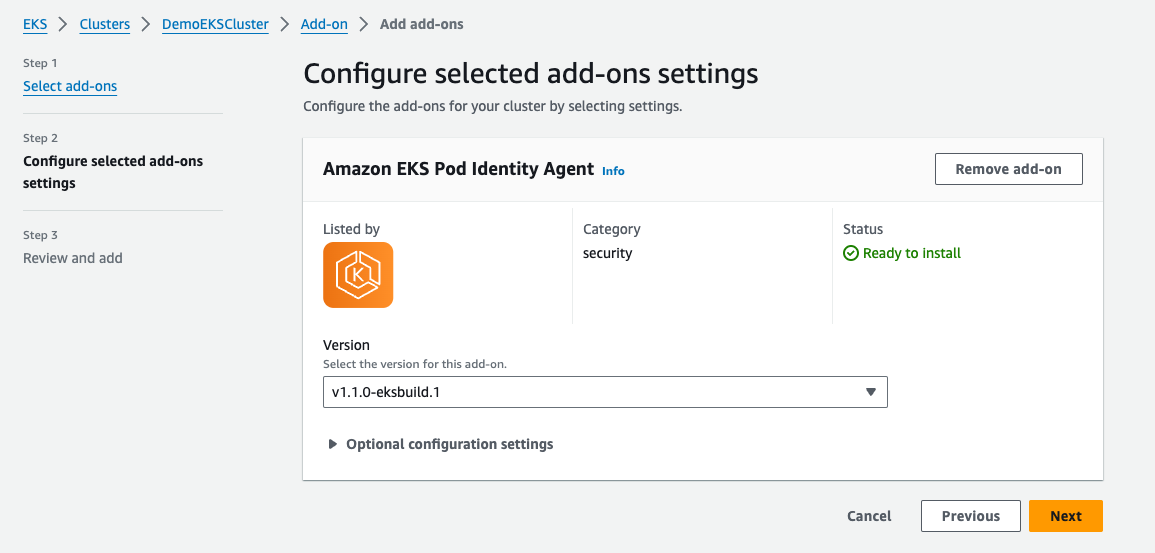
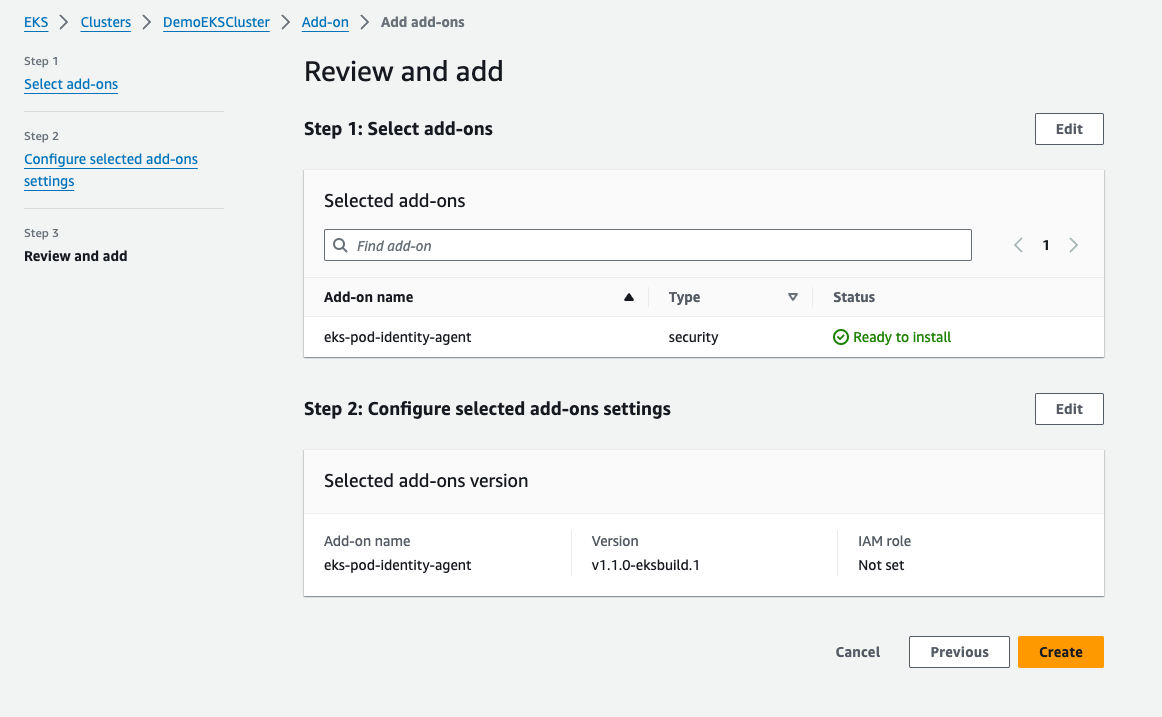
Next, I installed the Amazon EKS Pod Identity Agent in my existing EKS cluster. In the EKS dashboard, I selected my cluster, navigated to the Add-ons tab, and chose Get more add-ons. Here, I added the EKS Pod Identity Agent. I stuck with the default settings, clicked Next, reviewed the configuration, and created the add-on. Within minutes, it was active in my cluster.
Create a Namespace and Service Account in Kubernetes
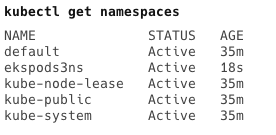
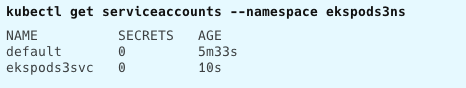
Creating a namespace in Kubernetes was my next step, allowing me to partition cluster resources. I opened my terminal and ran kubectl create namespace ekspods3ns. After verifying its creation, I moved on to create a service account within this namespace using kubectl create serviceaccount ekspods3svc --namespace ekspods3ns.
Map IAM Role to Kubernetes Service Account
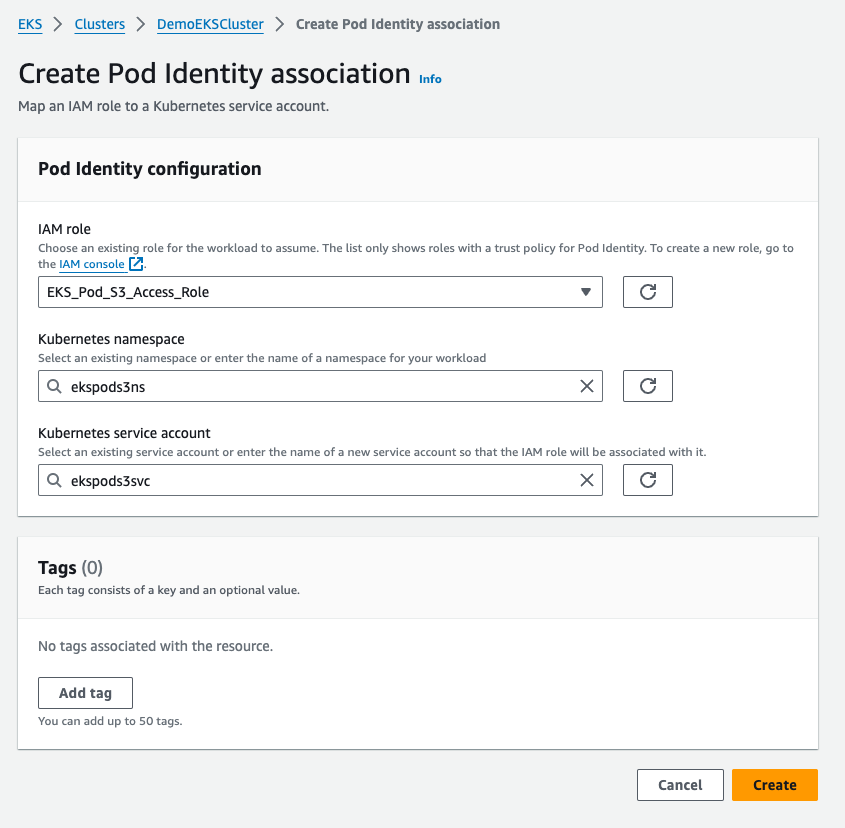
With the Amazon EKS Pod Identity add-on, namespace, and service account added to my cluster, it was time to link the IAM role to my Kubernetes pods. In the EKS cluster’s Access tab, I selected Create Pod Identity association under Pod Identity associations, choosing the IAM role and service account I had just created.
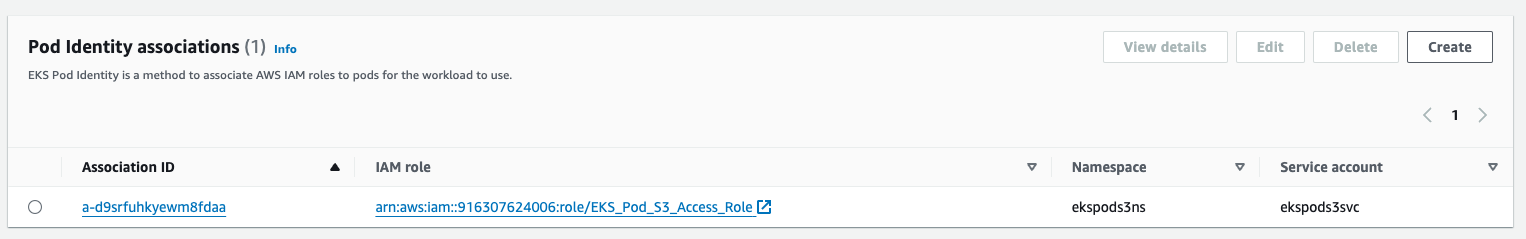
Testing the EKS-to-S3 Integration
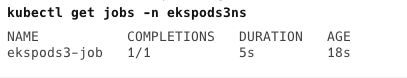
Deploying my application pod in the Amazon EKS cluster was the actual test. I cloned my Git repository containing the Kubernetes manifest file ekspods3-job.yaml, and applied it to my EKS cluster using kubectl apply -f ekspods3-job.yaml. To monitor the job, I used kubectl get jobs -n ekspods3ns.
Upon reviewing the manifest, you will notice that I have utilized the namespace and service account I created in the previous steps to apply the EKS Pod Identity IAM Role mapping for the pod.
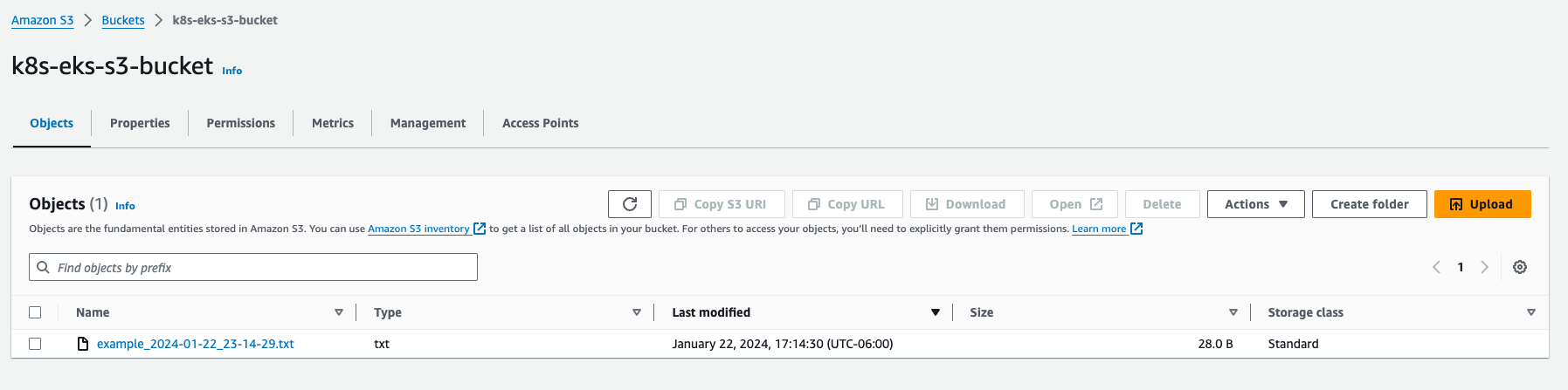
Expected Outcome
The job successfully created a pod in my EKS cluster that ran the Docker container. This container executed the script and uploaded a file to my S3 bucket. I verified the upload through the AWS S3 console.
Wrap-Up
Using Amazon EKS Pod Identity, I significantly simplified AWS service access in Kubernetes applications. This journey has shown me how to manage access to AWS services like S3 securely and efficiently in an EKS environment.
